this one’s been brewing for a while.
I’ve been building the economic proof that privacy creates value, the dual agents to realise this as self sovereign—the equations, the multipliers, the 31,000× gap between sovereign and surveillance architectures. But equations don’t transact. You can prove the value exists and still have no mechanism to realise it.
That’s the gap MyTerms fills.
We met through IIW and Project VRM day. Same problem, different angles Iain Henderson. 35+ years in advertising and CRM watching surveillance-based targeting systematically fail on one side. Modelling why it fails mathematically and socially on the other. Turns out we’re building layers of the same stack.
MyTerms—IEEE P7012—provides what the Privacy is Value thesis has been missing: the agreement layer. Bilateral contracts where individuals propose terms. Organisations accept or don’t get access.
Launches January 2026. This felt like the right moment to write together.

MyTerms Is The Agreement Layer,
The core insight is simple:
flip who proposes the terms.
Right now every digital interaction starts with the organisation’s terms. Privacy policies nobody reads. Cookie notices that mean nothing. Consent checkboxes that provide legal cover while enabling extraction. The digital world we were promised became surveillance, spam, AI slop, fraud.
MyTerms inverts this. The individual proposes. Organisations accept those terms to receive data.
IEEE P7012—nicknamed MyTerms, the same way 802.11 is nicknamed Wi-Fi—creates a subset of the Internet where personal data exchange is transparent and equitable. No surveillance. That’s not an optional feature. It’s foundational to every agreement type.
Four principles built into every MyTerms agreement:
Transparency: Be clear about what you’re asking for and what you’ll do with it
Data Minimisation: Don’t ask for more than you need
Purpose Limitation: Don’t do more than we agreed to
Reciprocity: Data flows two ways—I keep access to my own data
These aren’t controversial. They’re common sense that got routed around for twenty years. MyTerms put muscle behind them, arms you with the swordsman’s first blade, forged with zero knowledge.
Each agreement comes in three formats:
plain language (one page max),
machine readable (for agents to parse), and
legal (for courts to enforce).
All linked to the W3C Data Privacy Vocabulary, permanent definitions for every key term. When an agreement references a DPV term, it comes with a name, definition, and persistent URL that won’t shift meaning over time.
The Surveillance Wastelands Proves the Model
Here’s a number that should anchor everything: $600 billion annually in global digital advertising. The MIT Media Lab’s Human Context Protocol paper points out this entire industry
“fundamentally operates on the logic of reducing search frictions and facilitating product discovery.”
Six hundred billion on matching buyers to sellers. The waste is far higher than Wanamaker’s famous “half.” 35+ years in the industry confirms it.
Why? The data is compromised at the source.
Current intent data—the signals that supposedly indicate who’s “in market” for what—comes from surveillance. Website visits, content downloads, search queries, behavioral tracking across platforms. This data is observed or derived, scraped from behavior that users often don’t know is being monitored, processed through opaque algorithms, and sold through broker networks with questionable provenance.
The individual is passive in this system. They didn’t consciously declare their requirements. They don’t know what’s been inferred about them. They certainly never agreed to participate in the matching market at all.
This creates a fundamental quality problem that no amount of algorithmic sophistication can solve.
The Privacy is Value model quantifies this. The value equation:
V_twin = P^1.5 · C · Q · S · e^(-λt) · (1 + N/N₀)^k · R(d) · M(u,y) · Φ(S⊥⿻⊥M)
🔐^✨ · 🔑 · ✅ · 🌐 · ⏳ · 🕸️^🌱 · 🎯 · 💰 · ⚖️(⚔️⊥⿻⊥🧙)🙂
Where:
P = Privacy preservation (0-1 scale)
C = Control factor (who holds the keys)
Q = Data quality / verifiability
S = Signal richness / context depth
R(d) = Reconstruction difficulty (dual-agent architecture guarantees R < 1)
M(u,y) = Market maturity factor
Φ(S⊥⿻⊥M) = Golden duality multiplier (collapses to 0.3-0.4 for split privacy)
The critical insight: P appears with an exponent (γ = 1.5). Privacy isn’t a linear factor—it’s exponential. Going from 90% privacy preservation to 95% doesn’t create 5% more value. The multiplicative effects compound.
With surveillance-derived data: P = 0.1, C = 0.05, Q = 0.30. The multiplicative factors destroy value before matching even begins. The $600B industry is spending enormous resources on signals that are mathematically degraded at the source.
The waste isn’t a failure of algorithms or targeting sophistication. It’s inherent to the data type. Surveillance-derived intent is low-value intent. No amount of processing can fix that.
Two Kinds of Intent
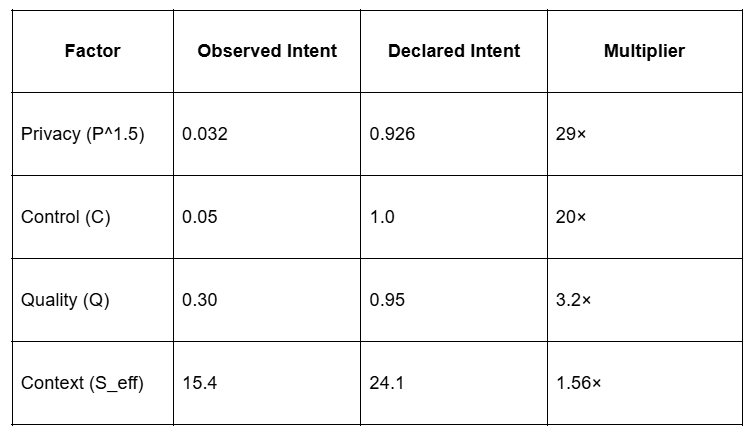
The model clarifies something practical experience has pointed toward for years: there are two fundamentally different kinds of intent data.
Observed/Derived Intent: Data collected through surveillance and tracking (adtech, martech, data brokers). The individual is passive. Provenance is opaque. The “intent” is an inference made by systems the individual never consented to and may not know exist.
Declared Intent: Data consciously shared by the individual in order to solicit responses. The individual is active. Provenance is clear. The intent is a genuine commitment to engage with qualified offers.
These are not two points on a spectrum. They are categorically different data types with categorically different value profiles.
Applying the value model:
The factors multiply. Total value differential: approximately 17× at minimum. With v3 model refinements including reconstruction difficulty and golden duality factors, the gap extends toward 31,000× under optimal conditions.
One qualified signal from declared intent is worth dozens of surveillance-derived “hot leads” that were never actually hot.
“Intent on MyTerms”—a fundamentally different data type than observed intent. The individual consciously goes to market to solicit responses. Individual equivalent of a B2B Request for Information.
The economics are too stark to ignore. Organisations will figure this out.
You now get it too, begin with things on your terms. Lead with the blade.
Promise Theory Connection
There’s theoretical grounding here in Promise Theory—Bergstra and Burgess’s framework for autonomous agent coordination.
The key distinction:
Impositions: One party attempts to constrain another’s behaviour without consent.
Promises: One party voluntarily commits to a behaviour, creating reliable expectations.
Surveillance-derived intent is an imposition. You didn’t promise anything. Your behavior was observed, processed, sold without your participation in the meaning-making. The data collector imposes their interpretation of your behavior onto systems you never agreed to participate in.
Declared intent under MyTerms is a promise. “I am in market for X. I commit to engage with qualified responses. These are my terms.” This is a voluntary commitment that creates genuine obligations on both sides.
The semantic difference explains the quality gap:
Impositions create noise (individuals resist, ignore, or actively subvert inferences made about them)
Promises create signal (individuals have committed to behaviours they intend to follow through on)
No amount of algorithmic refinement can transform an imposition into a promise. The data type is fundamentally different. The value gap is inherent.
MyTerms implements what Promise Theory calls the invitation pattern.
Acceptance before proposal. You must accept my terms before I share my intent.
Surveillance implements the attack pattern. Extraction without consent.
That architectural choice can’t be retrofitted.
Why This Matters for the Dual-Agent Architecture
In the spellbook, this is Act 4: The Blade Alone—First Adventures.
The Swordsman protects boundaries. Guards what enters and exits. Enforces terms. Revokes access when agreements break. But protection needs instruments.
MyTerms agreements are that instrument:
Sign these terms or receive no data
Violate the agreement, lose access
Machine-readable means agents can enforce programmatically
Bilateral means both parties have signed commitments
The Mage operates within boundaries the Swordsman enforces. Composing Intentcasts, managing responses, coordinating with qualified counterparties. Delegation inside protected space.
From the CRM side, the same insight: personal agents—fiduciary agents working for individuals—need a handshake protocol. When your agent goes to market on your behalf, it needs terms the counterparty’s agent can parse, evaluate, accept or decline.
Machine-readable bilateral agreements make agent-to-agent coordination possible without surveillance infrastructure.
The dual-agent architecture maintains structural separation between privacy enforcement and delegation optimisation. A unified agent that handles both faces an inherent conflict of interest—the same system that wants to extract maximum value from matching is responsible for protecting the individual from exploitation. Under pressure to deliver results, the delegation function erodes the privacy function.
Mathematical modelling shows that attempts to split privacy functions collapse the value equation. The fusion factor (F) measures unified vs. split privacy:
F = 1.0 (unified): Full value realization
F = 0.3-0.4 (split): 62.5%+ value destruction before other factors apply
The dual-agent architecture maintains F = 1.0 by making privacy enforcement structurally independent from delegation optimization.
The First Five Agreements
Five standardized agreements launching with January 2026 market feedback mode:
Relationship Agreements:
SD-BASE: Base service delivery relationship. Default for agents proposing MyTerms. “Just give me your service, nothing more.” No tracking. Yet. Negotiation toward additional provisions comes after that baseline is established.
SD-BASE-DP: With data portability—your own instance of relationship data. You keep access to everything the organization knows about you.
Data Contribution Agreements:
PDC-AI: Data for AI training, under your terms. If organizations want to train on your data, they sign your agreement specifying exactly how.
PDC-GOOD: Data for Good projects. Contributing to research, public benefit initiatives, social good—still under bilateral terms.
PDC-INTENT: The Intention Economy enabler. Intentcasting. This is the individual equivalent of an RFI/RFP—going to market with structured requirements, inviting qualified responses under your terms.
The MyTerms Alliance—global network of founding partners—is forming. Organisations signing on demonstrate belief in bilateral standards, commitment to operating where data exchange is transparent and surveillance-free.
A Verification Problem
Here’s where the two projects connect directly.
MyTerms provides excellent agreement infrastructure. But agreements without enforcement are just paper. How do you verify that an organisation accepting your PDC-INTENT terms actually honours them? How do you ensure their agent is genuinely fiduciary rather than surveillance in a fiduciary wrapper?
This matters because the current compliance regime is theatrical. Organisations sign terms of service that nobody reads, operate however they want, and face consequences only when caught—usually years later, usually with fines that amount to cost of doing business. The structural incentives reward violation.
MyTerms shifts enforcement architecture. Bilateral contracts create legal standing. Machine-readable terms enable automated monitoring. But enforcement still requires verification infrastructure.
This is the problem the agentprivacy protocol addresses.
Verifiable Relationship Credentials (VRCs):
Cryptographic attestations of relationship quality, issued bilaterally between parties who have successfully transacted. VRCs are not authority-issued credentials (”this entity is certified”)—they’re peer attestations (”I have interacted with this entity and can attest to their behaviour”).
When an organisation’s agent wants to receive MyTerms Intentcasts, it can present VRCs from previous bilateral relationships demonstrating a track record of honouring terms. This creates reputation without surveillance—attestations flow from actual relationships, not from monitoring behavior across contexts.
The bilateral nature is critical. A VRC requires attestation from both parties. Neither side can unilaterally inflate reputation. Gaming VRCs requires actually building genuine relationships—which is the behavior we want to incentivise anyway.
Relationship Proverb Protocol (RPP):
Comprehension verification at 125:1 compression. Before receiving privileged data, an agent must demonstrate understanding of the bilateral terms—not just signature, but semantic grasp. The proverb protocol requires agents to summarise agreements in ways that prove genuine comprehension.
This addresses a real attack vector: agents that sign MyTerms agreements but operate in ways that violate the spirit while technically complying with the letter. Adversarial compliance. Comprehension verification creates an additional barrier.
The compression ratio becomes a measurable trust metric. Can your agent compress the agreement to a proverb that captures its essence? 125:1 compression without semantic loss distinguishes genuine understanding from sophisticated pattern matching. Different contextual framings should produce the same underlying principles, what we call;
“story fracture, principle convergence.”
Zero-Knowledge Proofs for Compliance:
Rather than trusting organisations to self-report, ZK proofs can demonstrate that specific behaviors occurred (or didn’t occur) without revealing underlying data. An organisation can prove “we did not share this individual’s data with third parties” cryptographically.
This is the cryptographic enforcement layer. ZK proofs enable audit without exposure. An organisation can demonstrate compliance with data minimisation requirements without revealing what data they hold. They can prove purpose limitation without revealing what purposes they considered. The verification is mathematically sound rather than trust-based.
MyTerms specifies what should happen. The verification layer confirms it did.
The People Built This
Standards don’t emerge from nowhere. the mages spell becomes the village weather.
Doc Searls chairs the Machine Readable Privacy Terms Working Group under IEEE’s Society on Social Implications of Technology. His book The Intention Economy (2012) laid the foundation—customers as source of intent signals rather than passive surveillance subjects. Fourteen years later, deployable infrastructure.
Customer Commons stewards MyTerms—agreement templates, standard’s public presence, alliance coordination. The three-format approach came from years making bilateral agreements practical.
W3C Data Privacy Vocabulary provides the terminology backbone. Every key term links to permanent definitions.
Project VRM has been iterating on vendor relationship management since 2006. Two decades of groundwork.
MyData Global has been building the human-centric data movement since 2016—annual conferences, the MyData Declaration signed by over 1,700 individuals and organisations, local hubs across 40+ countries on six continents. Their purpose: empower individuals by improving their right to self-determination regarding their personal data. They established the global coalition that made standards like MyTerms politically viable, connecting entrepreneurs, activists, academics, corporations, public agencies, and developers around one common goal. When we talk about a fair, sustainable, and prosperous digital society, MyData built the community that keeps that vision alive.
And now… MyTerms
This is real infrastructure. Standards body, working group, chair thinking about this for fourteen years, communities building pieces across two decades. Not a startup MVP—institutional infrastructure designed to last.
The Integration with the Trust Graph
MyTerms provides agreements. The agentprivacy protocol provides verification they’re honored.
The Trust Graph Plane: A peer-to-peer network of VRC attestations enabling discovery of trustworthy counterparties. When an individual publishes an Intentcast, the Trust Graph surfaces organisations with:
Track records of honoring MyTerms agreements (attested by previous counterparties)
Verified comprehension of the specific agreement type
Cryptographic proof of compliance infrastructure
This isn’t a centralised reputation system. It’s emergent trust from bilateral attestations. Organisations earn visibility by building genuine relationships, not by gaming algorithmic metrics.
The infrastructure builds on work from the First Person project—developing the identity and data sovereignty primitives that make bilateral attestation possible at scale. First Person’s focus on individual-controlled identity provides the foundation layer: you can’t have genuine bilateral agreements without genuine individual agency over identity. The Trust Graph extends that foundation into relationship discovery.
MyTerms Alliance Guild-based distribution: Specialised communities with their own trust requirements and agreement templates. A healthcare guild might have stricter data handling requirements than a retail guild. A financial services guild might require additional compliance attestations.
MyTerms agreements can be specialised by guild context while maintaining the core bilateral, no-surveillance foundation.
What’s Onward
Near-term: VRC attestations referencing MyTerms agreement types. Organisations honoring PDC-INTENT consistently accumulate attestations new Intentcasters can verify. Specification alignment ensuring VRCs and MyTerms work together cleanly.
The January 2026 launch puts market feedback mode live. Six months of learning how bilateral agreements work in practice. Which friction points emerge. What organisations need to participate. What individuals actually want from the system.
Medium-term: Trust Graph discovery of MyTerms-qualified counterparties. Reference implementation demonstrating the full flow from Intentcast through Trust Graph discovery through bilateral relationship establishment. Publish Intentcast → surface organisations with bilateral compliance history → establish verified relationships → receive qualified responses.
The Trust Graph isn’t a centralised registry. It’s emergent discovery through VRC attestation chains. When you publish an Intentcast, your agent queries the graph for organisations with relevant track records. Organisations with strong bilateral histories surface naturally. New entrants can build reputation through demonstrated behavior rather than purchased credentials.
Longer-term: Guild-specific variants. Healthcare with stricter handling requirements and additional compliance attestations. Financial services with regulatory alignment and audit trails. Retail guilds optimised for high-volume, lower-sensitivity matching. Each guild maintains the core bilateral, no-surveillance foundation while adding domain-specific requirements.
The guild structure enables progressive trust building. Start with low-stakes interactions in one domain. Accumulate VRCs. Carry that reputation into higher-stakes guilds as track record justifies access. Organisations can’t buy their way into high-trust guilds—they earn access through demonstrated behavior.
Both projects committed to open standards. IEEE standardisation. W3C vocabularies. CC0/CC-BY licensing. Success measured by whether bilateral privacy-preserving exchange becomes normal—not whether our implementations dominate.
The Economic Transformation
If this works, the matching market transforms in phases.
Phase 1: Waste Elimination.
Organisations rationally shift budget toward higher-value signals. Even conservative estimates of current waste (60-70% of $600B) imply hundreds of billions in potential reallocation. The 17× gap creates immediate arbitrage opportunity for early adopters.
Phase 2: Market Expansion.
Declared intent opens markets surveillance can’t serve:
High-sensitivity purchases (healthcare, financial, legal) where individuals currently avoid leaving digital trails
Complex requirements that need richer context than behavioural observation captures
Trust-dependent transactions where individuals need to demonstrate trustworthiness through peer attestation rather than surveillance scores
Surveillance creates cold markets in sensitive domains. People avoid digital trails precisely because they fear surveillance. MyTerms makes those markets accessible by eliminating the surveillance that makes people avoid them.
Phase 3: New Economic Forms.
Bilateral agreement infrastructure enables economic structures that don’t exist today:
Intentcast aggregation: buyer groups shaping market offerings rather than waiting for sellers to create deals
Relationship-based pricing: verified reputation through VRCs enabling better terms for trustworthy counterparties
Fiduciary agent economics: AI agents with genuine professional obligations analogous to doctors, lawyers, financial advisors
The fiduciary agent economy is particularly significant. Agents operating under genuine fiduciary duty—legally binding, cryptographically enforced—can earn compensation aligned with individual outcomes rather than platform extraction. This creates a new professional category with real accountability.
The Window
2-3 years before surveillance architectures achieve network effects making alternatives unviable. Infrastructure must be foundational, not retrofitted.
MyTerms launching January 2026 matters. Market feedback begins. Organisations discover MyTerms agreements create more value than surveillance data. Individuals discover they can engage on their own terms.
The 17× value gap—extending toward 31,000× under optimal dual-agent conditions—is too large to ignore indefinitely. Organisations will figure out that one qualified MyTerms Intentcast is worth dozens of surveillance-derived “hot leads.” Then they’ll do the obvious thing.
The 7th Capital
Step back far enough and the pattern becomes clear.
We’ve been here before. Every form of capital goes through the same evolution: discovery, extraction, enclosure, contestation, property rights, productive deployment. Land. Labor. Financial capital. Intellectual property. Social capital. Natural capital.
Behavioral data is the 7th. And we’re in the feudal phase.
The surveillance economy isn’t some inevitable endpoint of digital technology. It’s a temporary arrangement—a blip where those who seized the asset first are extracting value before property rights get sorted out. Feudalism wasn’t the natural order of agricultural society. It was a transitional structure that emerged when land became valuable and property rights hadn’t yet developed to allocate it efficiently.
We’re watching the same pattern, only on 10x speed. Behavioural data became valuable. Those with infrastructure to capture it… did. They built extraction systems optimised for their benefit, not for productive allocation of the underlying asset. The result: massive waste. The $600B matching market running on degraded signals. Value destroyed at source because the property rights aren’t established.
The economics haven’t changed since Adam Smith. Supply and demand. Voluntary exchange. Price discovery. Comparative advantage. What’s changed is we have a new asset class, and we’re still working out who owns it and how to get productive use from it.
The surveillance model says: the asset belongs to whoever can capture it. Extract maximum value. Resist any property rights that would constrain extraction.
The sovereign model says: the asset belongs to the individual who generates it. Establish property rights. Enable voluntary exchange. Let supply meet demand through bilateral agreement.
The math is clear on which produces more value. 17× minimum. 31,000× under optimal conditions. The feudal model isn’t just ethically questionable—it’s economically inferior. It destroys the asset it extracts.
History suggests where this goes. Property rights get established. Extraction gives way to production. The asset gets allocated to its highest-value use through voluntary exchange rather than seizure.
The future is genuinely bright. Bilateral privacy-preserving exchange. Fiduciary agents. Trust graphs. Intent markets. New economic forms we can barely imagine from inside the feudal blip.
But we need the first blade.
The Blade—privacy as boundary-making, the power to cut between what is revealed and what remains hidden, the defensive art that says "this far and no further."
MyTerms is that blade. The Swordsman’s instrument. The mechanism that enables individuals to assert property rights over their behavioural data. Without it, the economics remain theoretical. The 7th capital stays enclosed by those who seized it first.
With it, supply meets demand. Properly.
Privacy is value.
The agreement layer makes it transactable.
Take back the 7th capital.

MyTerms: myterms.info
Customer Commons: customercommons.org
Project VRM: projectvrm.org
DataPal: datapal.me
agentprivacy: agentprivacy.ai
First Person Spellbook: agentprivacy.ai/story
agentprivacy research: github.com/mitchuski/agentprivacy-docs
In collaboration with:
just another mage, privacymage and Henderson, sharing their spellbooks.
(⚔️⊥⊥🧙♂️)🙂






Brilliant piece on the bilateral agreement infrastructure problem. The 17x value differential betwen declared vs observed intent makes so much sense when I think about my own behavior online, I actively avoid digital trails for sensitive purchases precisely because of the surviellance, which creates those cold markets you mentioned. The feudal capital comparison is spot-on too, we really are just watching property rights get sorted in real-time for behavioral data, same pattern just on fast-forward.