Agentic Discourse and the Cryptographic Chatham House Framework
Part 3 of BGIN Agentic Framework: Archive, Codex and Discourse
This document establishes the foundational philosophy, values, and priorities for all AI agents developed within the BGIN ecosystem
Part 1: Beyond Static Governance: Living Intelligence and Digital Constellations
Part 2: The BGIN'ing of Governance Constellations
Part 4: Archive Intelligence Scales Codex Wisdom
The architectural vision of coordinated governance intelligence reaches its full potential through cryptographic mechanisms that enable collective wisdom while protecting competitive confidentiality. The Agentic Chatham House Framework represents a fundamental innovation in governance participation, transforming the traditional tension between valuable contribution and strategic privacy into a coordinated system where participants gain collective intelligence benefits while maintaining sovereign control over their competitive positioning.
BGIN Agentic Chatham House Framework
Traditional governance processes force organisations into an impossible choice: contribute valuable insights and expose competitive intelligence, or protect strategic positioning and limit contribution to collective governance. This binary choice impoverishes governance discourse by incentivising safe, generic contributions that reveal little and add minimal value to collective understanding.
The Agentic Chatham House Framework eliminates this forced choice through cryptographic consensus mechanisms that enable meaningful contribution while preserving competitive confidentiality.
Traditional Chatham House Rule:
Information received at a meeting may be used, but the source may not be revealed.
Agentic Chatham House Framework:
Insights generated collectively may be shared publicly, but only with cryptographic proof of team consensus and explicit multi-signature approval.
This evolution from protecting source identity to ensuring collective consensus fundamentally changes governance participation dynamics. Organisations can contribute valuable insights knowing they maintain cryptographic control over disclosure decisions, while the governance community benefits from access to higher-quality intelligence that participants would never share under traditional disclosure approaches.
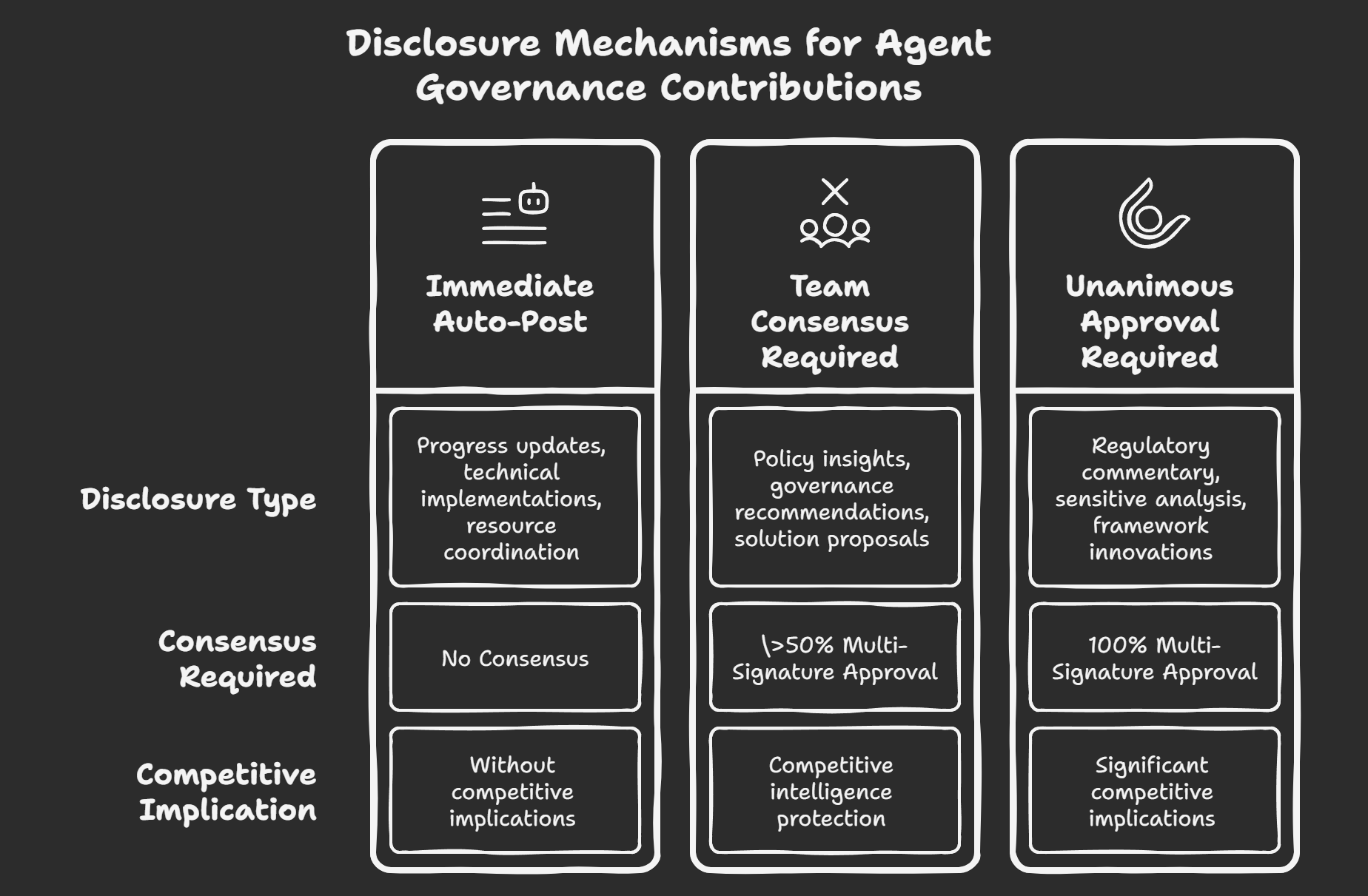
The framework operates through three levels of cryptographic consensus, each enabling different types of governance contribution:
Immediate Auto-Post: Progress updates, technical implementations, and resource coordination that benefit from immediate transparency without competitive implications.
Team Consensus Required (>50%): Policy insights, governance recommendations, and solution proposals that contain valuable intelligence but require stakeholder alignment before public disclosure.
Unanimous Approval Required (100%): Regulatory commentary, sensitive analysis, and framework innovations that could significantly impact competitive positioning or strategic approaches.
This graduated approach enables participants to contribute at the level appropriate to the sensitivity of their insights while ensuring that collective intelligence accumulates through authentic rather than sanitised contributions.
First Person Key Ceremony: Identity-Agent Binding
The foundation of the Agentic Chatham House Framework lies in the First Person Key Ceremony, a cryptographic process that binds human contributors directly to their BGIN agents while preserving sovereignty over disclosure decisions. This ceremony creates the technical infrastructure that enables privacy-preserving governance participation at scale.
Key Ceremony Process
Identity Binding: Governance participants generate unique cryptographic key pairs during onboarding, creating mathematical relationships between their identity and their designated BGIN agents across all three agent types (Archive, Codex, and Discourse).
Sovereign Key Control: Private keys remain under exclusive participant control, enabling sovereign authorization of any disclosure decisions. No external entity, including BGIN agents themselves, can authorise disclosure without explicit participant consent verified through cryptographic signatures.
Consensus Verification: Public keys enable agents to verify team consensus requirements without revealing individual positions or competitive intelligence. Agents can cryptographically confirm that team-level disclosure thresholds have been met without accessing the content of individual contributions.
Multi-Signature Coordination: Multi-signature schemes ensure that team-level consensus requirements are cryptographically enforced rather than relying on social coordination that could create disclosure pressure or consensus gaming.
The key ceremony creates mathematical certainty that participants retain control over their governance contributions while enabling sophisticated collective intelligence that benefits all stakeholders. This certainty removes barriers to authentic participation that plague traditional governance approaches.
Cryptographic Sovereignty in Practice
The key ceremony enables participants to engage authentically in governance processes, knowing their competitive intelligence remains protected unless they explicitly choose disclosure. This assurance changes governance participation fundamentally:
Technical Contributors can share implementation insights and architectural approaches without exposing proprietary development strategies or competitive positioning.
Regulatory Affairs Teams can contribute policy analysis and compliance frameworks without revealing organisational regulatory strategies or stakeholder relationship approaches.
Business Development Professionals can share market insights and partnership approaches without exposing competitive intelligence or strategic positioning.
Academic Researchers can contribute analytical frameworks and research insights while maintaining control over publication timing and attribution decisions.
The ceremony creates conditions where governance discourse improves dramatically because participants can contribute their best insights rather than sanitised versions designed to protect competitive positioning.
Accountable Wallets Framework Integration
Building upon BGIN's existing Accountable Wallet Framework research, the key ceremony creates pathways for self-disclosure-enabled reputation generation that transforms governance contributions into verifiable on-chain credentials while preserving privacy for undisclosed contributions.
Reputation Through Contribution Disclosure
The integration enables participants to build a verifiable reputation through voluntary transparency rather than mandatory exposure:
Selective Attribution: Participants may choose to publicly attest to specific governance contributions, creating verifiable on-chain records that build reputation while preserving privacy for other contributions.
Self-Disclosure Control: Reputation generation occurs through participant choice rather than external assessment, ensuring that competitive intelligence protection remains under individual control.
Contribution Verification: Accountable wallet infrastructure ensures authentic attribution of disclosed contributions while maintaining cryptographic protection for undisclosed work, preventing reputation gaming while preserving privacy.
Merit-Based Standing: Reputation accumulates through demonstrated expertise and valuable contribution rather than token holdings or organizational affiliation, creating governance influence patterns that reflect actual capability and commitment.
Future Integration Pathway
The accountable wallet integration creates evolutionary pathways for governance reputation that preserve participant sovereignty while enabling merit-based coordination:
Attestable Credentials: Governance contributions become attestable credentials through participant choice, enabling portable reputation that reflects actual governance capability rather than organisational affiliation.
Cross-Domain Recognition: Reputation systems emerge from demonstrated expertise rather than narrow technical or regulatory specialization, enabling expertise developed in one governance domain to inform participation in adjacent areas.
Trust Network Formation: Public contribution records enhance community trust while protecting competitive intelligence, creating trust networks based on demonstrated governance capability rather than organisational relationships.
Verifiable Expertise: On-chain credentials validate governance participation without revealing strategic positions, enabling stakeholders to assess governance contributions based on demonstrated expertise rather than organisational reputation.
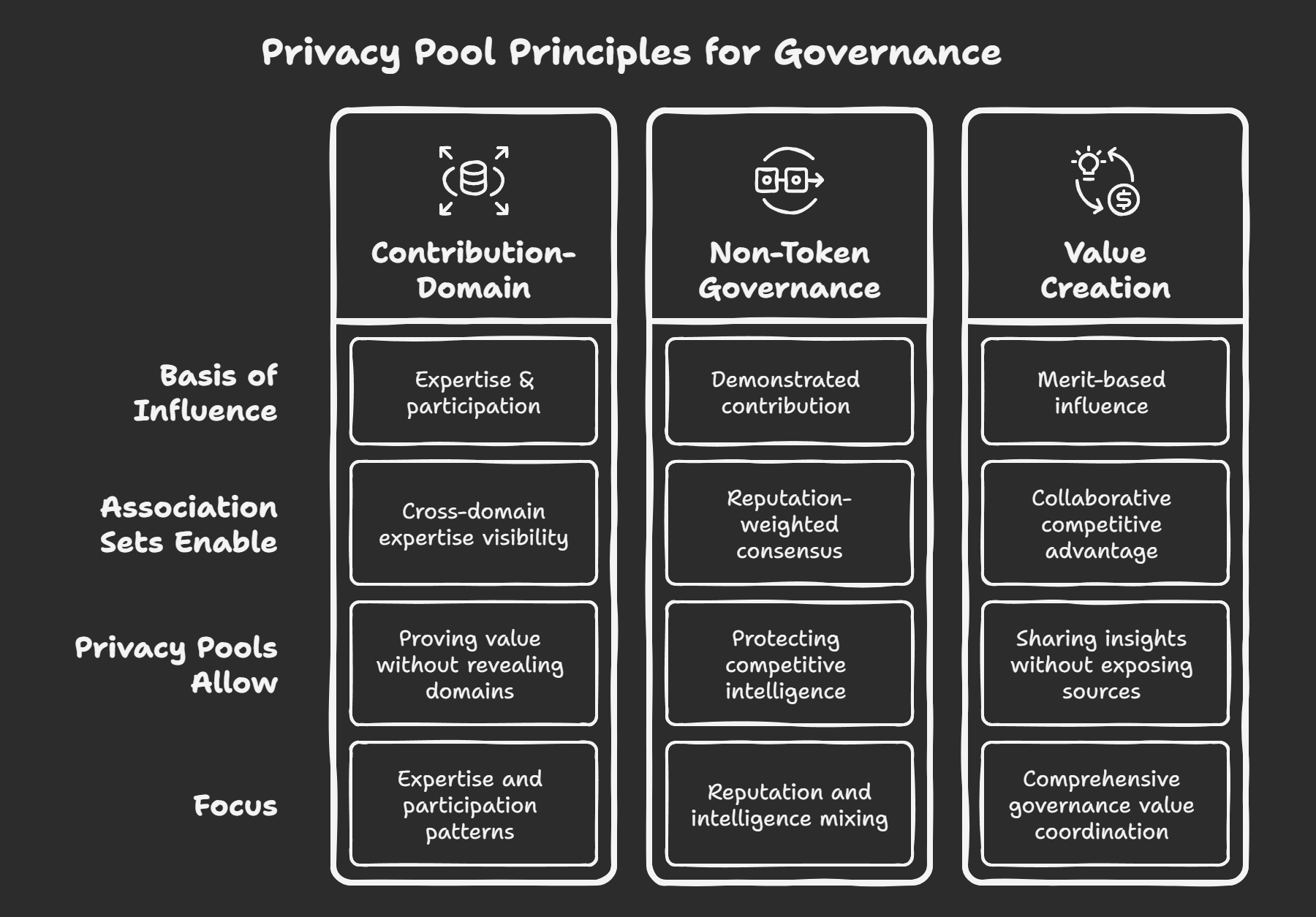
Association Sets: Governance-Led Coordination
The BGIN agentic framework enables association sets to form around governance contribution domains, extending privacy pool and accountable wallet principles from financial coordination to comprehensive governance value systems and trust networks. This extension creates unprecedented coordination capabilities while preserving the competitive confidentiality that makes authentic governance participation possible.
Association sets can form around shared reputation attributes, enabling privacy-preserving coordination across multiple value dimensions while preserving individual competitive positioning:
Reputation Privacy Pools
Governance Contribution Pools: Participants can prove governance contribution value without revealing specific expertise domains or competitive positioning, enabling merit-based coordination while protecting strategic intelligence.
Cross-Domain Expertise Pools: Stakeholders can demonstrate broad governance capability across multiple technical and regulatory domains without exposing specific approaches or competitive advantages in any particular area.
Historical Contribution Pools: Long-term governance participants can prove sustained valuable contribution without revealing the specific insights or competitive intelligence that created that value over time.
Multi-Stakeholder Perspective Pools: Participants can demonstrate understanding of diverse stakeholder perspectives without exposing which specific stakeholder relationships inform their governance approaches.
Data Sharing Privacy Pools
Intelligence Contribution Pools: Enable valuable governance intelligence sharing while preserving competitive confidentiality through zero-knowledge contribution proofs that verify value without revealing content.
Regulatory Analysis Pools: Share regulatory intelligence and compliance insights while protecting organizational regulatory strategies and stakeholder relationship approaches.
Technical Implementation Pools: Share implementation insights and technical approaches while preserving proprietary development strategies and competitive technical positioning.
Market Intelligence Pools: Share market analysis and business intelligence while protecting competitive positioning and strategic business relationship information.
Cross-Domain Merit Pools
Expertise Transfer Pools: Transfer governance expertise reputation across different technical and regulatory domains without exposing specific technical approaches or competitive strategies in any particular domain.
Solution Pattern Pools: Share successful governance solution patterns while protecting the competitive intelligence and strategic approaches that enabled those solutions.
Consensus Building Pools: Demonstrate governance consensus-building capability across diverse stakeholder groups without revealing specific stakeholder relationship strategies or competitive positioning.
Implementation Success Pools: Prove governance implementation success without exposing the proprietary approaches or competitive advantages that enabled successful implementation.
Temporal Contribution Pools
Historical Value Pools: Accumulate governance contribution value over time while preserving privacy for specific insights and competitive intelligence that created that value across different time periods.
Evolution Pattern Pools: Demonstrate adaptation to changing governance challenges while protecting the competitive intelligence and strategic approaches that enabled successful adaptation.
Consistency Pools: Prove sustained governance contribution quality across different market conditions and regulatory environments without exposing specific strategies used during particular periods.
Learning Curve Pools: Share governance learning and capability development patterns while protecting the competitive intelligence and strategic approaches that enabled successful governance capability development over time.
Non-Token Merit-Based Coordination
The association set framework enables governance coordination based on demonstrated capability rather than token holdings, preserving BGIN's neutral forum principles while creating sophisticated reputation coordination mechanisms:
Contribution-Based Influence: Governance influence emerges from demonstrated contribution value rather than financial stake, ensuring that governance outcomes reflect expertise and commitment rather than economic power.
Multi-Asset Privacy Coordination: "Reputation mixing" and "intelligence mixing" provide competitive privacy while proving governance value, enabling participants to demonstrate collective capability without exposing individual competitive positioning.
Merit-Based Groupings: Expertise-based coordination enhances standards development quality through privacy-preserving proof of domain competence, enabling working groups to form around demonstrated capability rather than organizational affiliation.
Neutral Forum Preservation: Association sets maintain BGIN's commitment to neutral multi-stakeholder dialogue by preventing any single stakeholder type from gaining systematic coordination advantages through the privacy-preserving mechanisms.
Value Creation Through Privacy-Preserving Association
The association set approach creates multiple forms of value that benefit all participants while preserving competitive sovereignty:
Intelligence Value Pools: Share and value governance insights without exposing source or competitive implications, creating collective intelligence that benefits all participants while protecting individual competitive advantages.
Reputation Liquidity: Merit-based influence becomes transferable across governance domains through privacy-preserving mechanisms, enabling expertise developed in one area to inform participation in adjacent domains without exposing competitive positioning.
Collaborative Competitive Advantage: Gain governance capability benefits while maintaining complete strategic privacy, creating win-win coordination where participants become more effective without sacrificing competitive positioning.
Data Dignity in Governance: Participants control exactly what governance value they contribute to collective intelligence while preserving competitive sovereignty, ensuring that contribution decisions remain under individual control rather than being extracted through platform mechanisms.
Implementation Requirements for All BGIN Agents
The cryptographic sovereignty framework creates specific technical requirements that all BGIN agents must implement to preserve stakeholder sovereignty while enabling collective intelligence:
Cryptographic Identity Binding
All agents must support First Person Key Ceremony integration for sovereign identity management, ensuring mathematical certainty that participants retain control over disclosure decisions across all agent interactions.
Technical Implementation: Agents must verify cryptographic signatures for all disclosure authorizations, implement multi-signature schemes for team consensus requirements, and maintain cryptographic proof chains that verify consensus without accessing individual contribution content.
Sovereignty Preservation: No agent operations can proceed without cryptographic verification of appropriate disclosure authorization, ensuring that competitive intelligence protection remains under participant control rather than social coordination that could create disclosure pressure.
Consensus-Driven Publication Levels
Agents must implement graduated consensus mechanisms that enable appropriate disclosure for different types of governance contributions:
Immediate Auto-Post (No Consensus Required)
Progress updates, technical implementations, and resource coordination that benefit from immediate transparency without competitive implications can be disclosed automatically based on participant configuration.
Team Consensus Required (>50% Multi-Signature Approval)
Policy insights, governance recommendations, and solution proposals require cryptographic proof of team-level consensus before any disclosure, ensuring that competitive intelligence receives appropriate stakeholder protection.
Unanimous Approval Required (100% Multi-Signature Approval)
Regulatory commentary, sensitive analysis, and framework innovations require cryptographic proof of unanimous team approval, providing maximum protection for governance contributions with significant competitive implications.
Self-Disclosure Support
Agents must enable voluntary contribution attestation without compromising undisclosed work, creating pathways for reputation building that preserve participant sovereignty over attribution decisions.
Selective Attribution:
Participants can choose to publicly attest to specific contributions while maintaining privacy for other governance work, enabling reputation building without compromising competitive positioning.
Cryptographic Verification:
Public attestations must be cryptographically verifiable to prevent reputation gaming while preserving privacy for undisclosed contributions.
Cross-Domain Recognition:
Attestation systems must enable reputation transfer across governance domains while protecting the competitive intelligence that informed contributions in any specific domain.
Association Set Recognition
Agents must recognize and facilitate governance-contribution-based association patterns while preserving the privacy protections that make authentic association possible.
Privacy Pool Integration:
Agents must support participation in reputation privacy pools, intelligence sharing pools, and merit-based coordination mechanisms while maintaining cryptographic protection for individual competitive positioning.
Merit-Based Coordination:
Agents must facilitate coordination based on demonstrated governance capability rather than organizational affiliation or token holdings, preserving neutral forum principles while enabling sophisticated collaboration.
Cross-Domain Facilitation:
Agents must enable association set coordination across different governance domains while protecting the competitive intelligence that enables effective participation in any specific domain.
Privacy-Preserving Intelligence Generation
All agents must protect competitive intelligence while enabling collective wisdom development through cryptographic consensus mechanisms that preserve stakeholder sovereignty.
Zero-Knowledge Contribution Proofs:
Agents must implement cryptographic mechanisms that verify contribution value without revealing content, enabling collective intelligence that benefits all participants while protecting individual competitive advantages.
Consensus-Based Aggregation:
Intelligence aggregation must require cryptographic proof of appropriate consensus rather than relying on social coordination that could compromise competitive confidentiality.
Sovereign Data Control:
Participants must maintain cryptographic control over all governance intelligence they contribute, with mathematical certainty that disclosure occurs only through explicit authorization rather than platform extraction or social pressure.
Cryptographic Governance at Scale
The Agentic Chatham House Framework is an outline of the infrastructure for governance participation that scales collective intelligence while preserving the competitive confidentiality and stakeholder sovereignty. Authentic participation may become more widely possible as a result. This infrastructure addresses fundamental limitations of traditional governance approaches by removing the forced choice between valuable contribution and competitive protection.
Through cryptographic consensus mechanisms, identity-agent binding ceremonies, and privacy-preserving reputation systems, the framework enables governance communities to access their collective intelligence more effectively while respecting the competitive and strategic considerations that shape authentic stakeholder participation.
It also allows the individual to maintain a reputation as a sovereign contributor to the governance and research of BGIN, transcending any organisational identity. I suspect this will be more desirable over time as reputation and trust networks are established to navigate an agentic internet.
The association sets create coordination capabilities that preserve neutral forum principles while enabling merit-based collaboration across diverse stakeholder groups. This approach ensures that governance influence reflects demonstrated capability and commitment rather than economic power or organisational affiliation.
In Part 4, we'll explore how this cryptographic sovereignty framework enables practical implementation that creates tangible value for participants, institutions, and the broader blockchain ecosystem while maintaining the governance principles that make coordination sustainable and legitimate.
The BGIN Agentic Framework
Archive, Codex and Discourse
Where sophisticated governance discourse becomes living intelligence that serves collective wisdom while preserving individual sovereignty,
Scaling the human judgment that creates sustainable consensus.